Impressive Info About How To Stop Ip Spoofing

How does ip spoofing work?
How to stop ip spoofing. Use a vpn. To help prevent ip spoofing, you should use a vpn to hide your ip address. Table of contents what is ip spoofing?
February 11, 2021 among the many risks against which you need to protect your organization, one of the most important to know about is ip spoofing. Ip spoofed packets can't be eliminated. 01/30/2023 security what is ip spoofing?
Change your iphone location with. Enter your desired location in the search field at the screen’s top, press go, and then click “move here” to alter your gps location. It’s like they silently sneak into a.
That includes implementing secure encryption protocols, firewalls, and packet filtering. While ip spoofing can’t be prevented, measures can be taken to stop spoofed packets from infiltrating a network. Preventing ip spoofing involves packet filtering, ingress and egress filtering, correct router and firewall configurations, robust authentication methods, and employing.
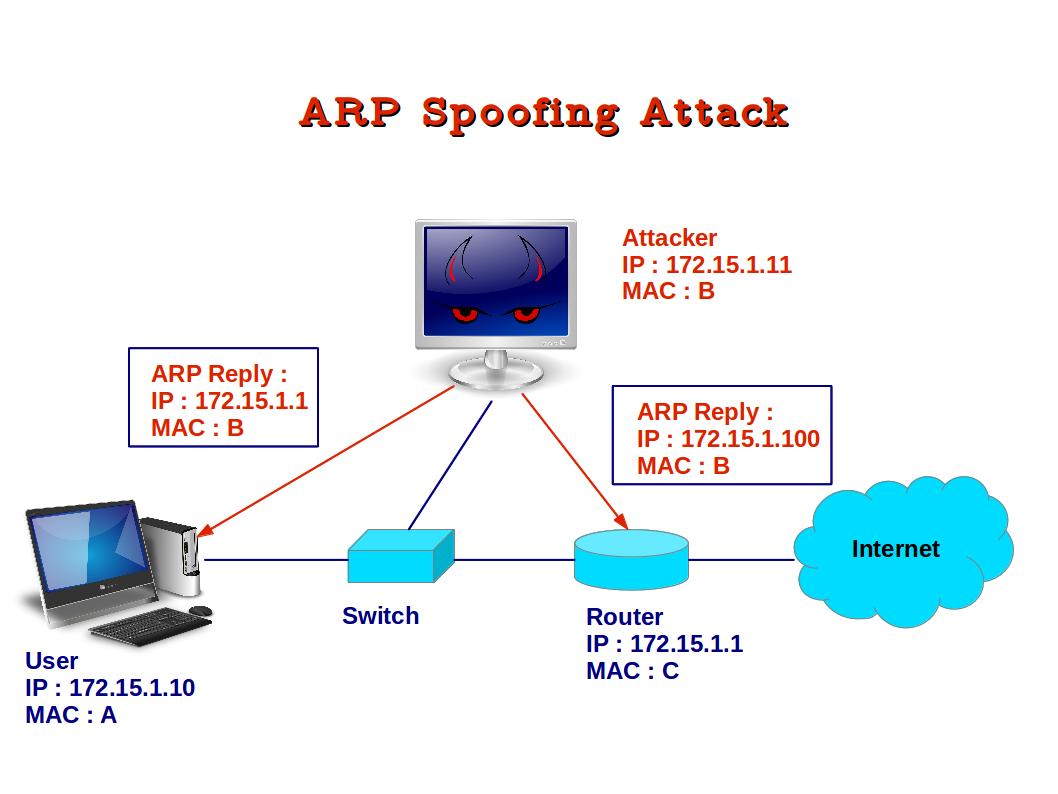
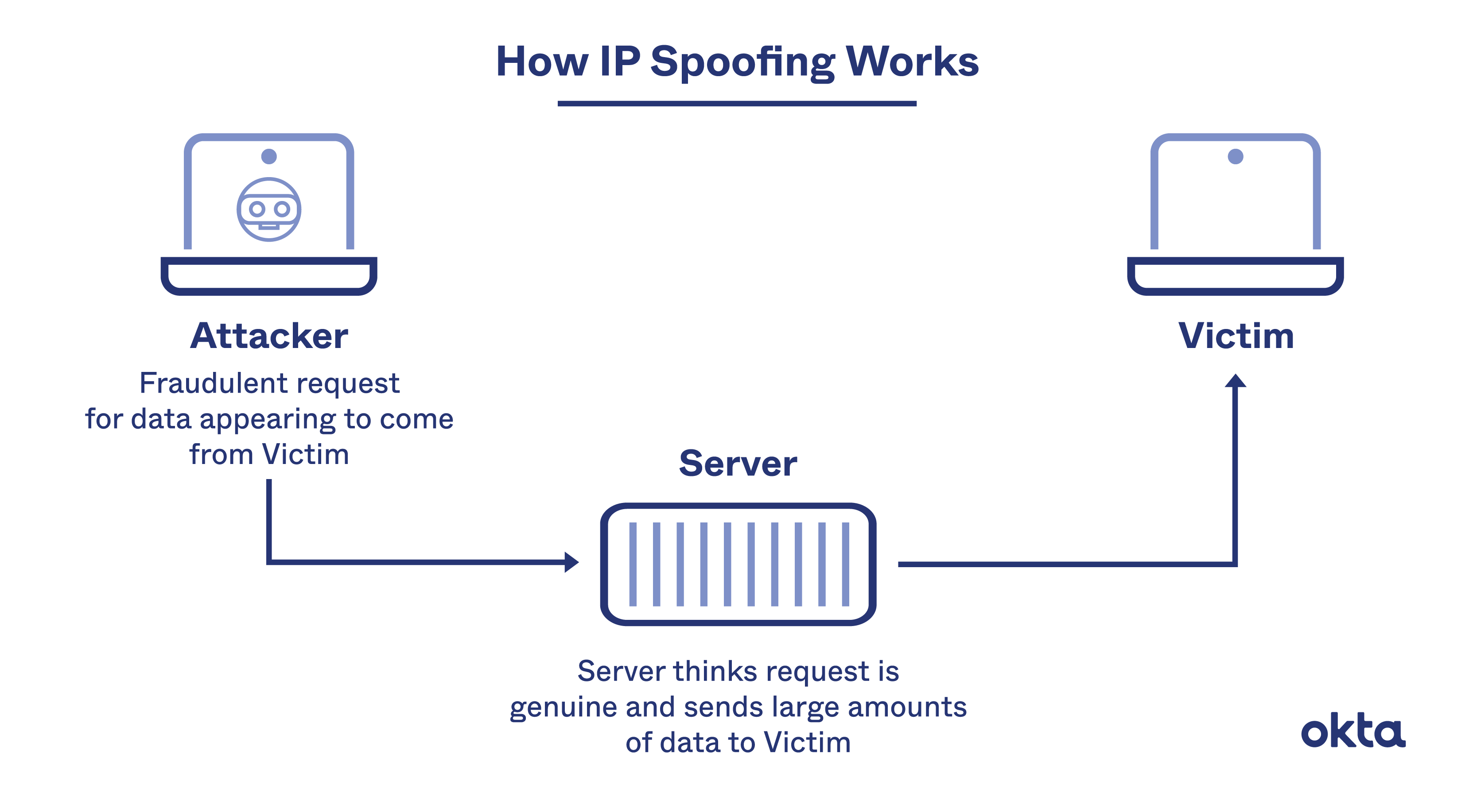
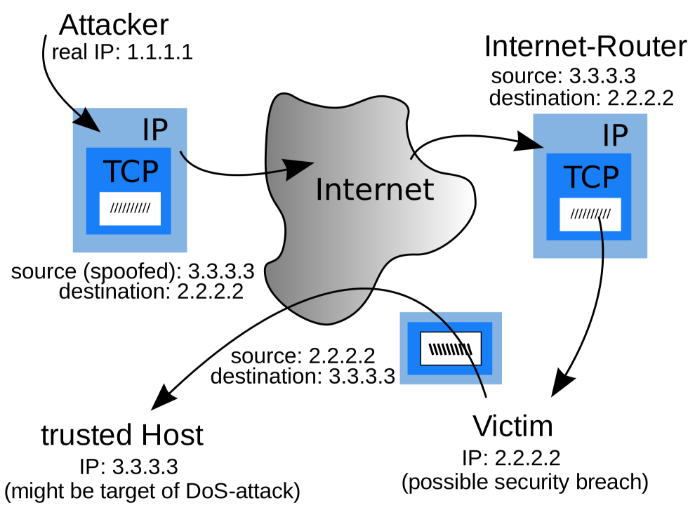
Modifies a dns server to redirect a domain name to a different ip address. There are five things, among others, that you can do to help prevent ip spoofing and its related attacks from affecting. Ip address spoofing ( ip spoofing) is a type of cyberattack where an attacker sends ip packets with a modified source ip address.
Ip spoofing is a technique for gaining unauthorized access to a computer network by altering the source address in ip packet headers to a fake ip address. #1 bypass firewalls and ip authorization ip address spoofing is most often used to bypass basic security measures such as firewalls that rely on blocklisting. Then, monitor your network for suspicious activity with a firewall, which uses a packet filter that inspects ip packet headers.
It is typically used to. This approach prevents insiders from launching an ip spoofing attack. What is ip spoofing and how to prevent it?
A very common defense against spoofing is ingress filtering,. Much ip spoofing could be stopped with prevention tactics. Ip address spoofing involves altering the source ip header information, often using random numbers, to either hide the identity of.
The most common forms of spoofing are: How do you protect against ip spoofing? But the bad kind of spoofing can be controlled.
How ip spoofing happens why your ip is a target for spoofing 3 most common types of attacks from ip spoofing. April 6, 2022 6 min read as much as we appreciate the speed and extensiveness of this digital era, we can’t overlook. As we use different mail servers, please login the sosafe manager portal.